 Lawsuit papers are usually pretty dull to read, but not this one!
Lawsuit papers are usually pretty dull to read, but not this one!
Rippling, Inc. (“The #1 HRIS Workforce Management System”) has filed a suit accusing competitor Deel of an amazing campaign of skullduggery and corporate espionage, orchestrated at the highest levels of Deel management, involving a sleeper agent, massive data theft, attempts to turn further spies, and more.
This case exposes a calculated and unlawful corporate espionage scheme, orchestrated by Deel, a global, multi-billion-dollar technology company. In a brazen act of corporate theft, Deel cultivated a spy to systematically steal its competitor’s most sensitive business information and trade secrets. This was not an isolated act of misconduct—it was a deliberate attack, perpetrated for over four months, designed to steal and weaponize critical competitive data, including a competitor’s sales leads, sales pipeline, and its entire playbook for pitching prospective clients.
And
Most shockingly, these espionage efforts appear to have been directed by the highest levels of Deel’s leadership, including, upon information and belief, Philippe Bouaziz – Deel’s Board Chair, Chief Financial Officer, and the father of the CEO – or those closest to him.
I wouldn’t want to be a Deel account executive fielding calls from customers right now.
According to the suit, Deel recruited a spy inside Rippling’s organization. This individual constantly searched the term “deel” in Rippling’s systems to discover where Deel was competing with Rippling, and what sales pitches, tactics, and offers Rippling was planning to use. The spy also discovered situations were a Deel customer was thinking of switching, presumably so Deel could quickly focus on retaining that customer.
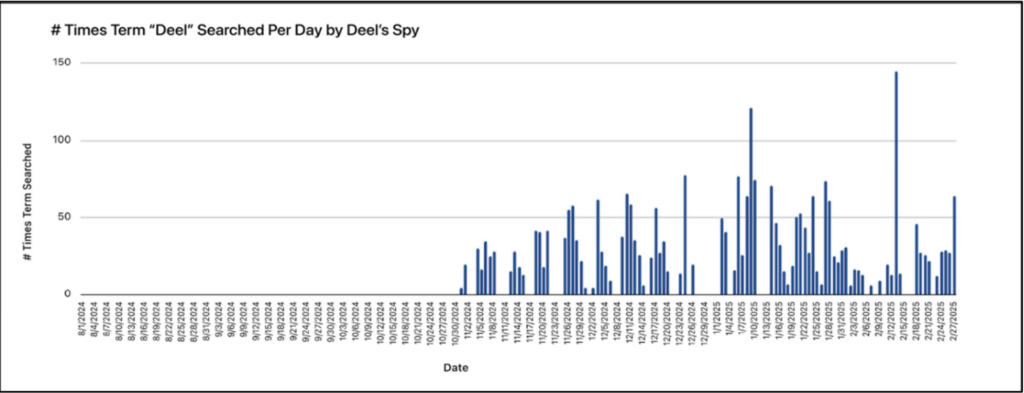
For example, on just one single day—February 21, 2025—Deel’s spy conducted searches that revealed 728 new companies requesting a demo of Rippling’s products; 282 in-depth notes from Rippling account executives on companies that were new prospects in its sales pipeline; and thorough information about 26 new deals with existing customers or prospective clients who were evaluating switching to Rippling directly from Deel. And that is just one single day. These activities were repeated nearly every single day, for over four months.
The Honeypot
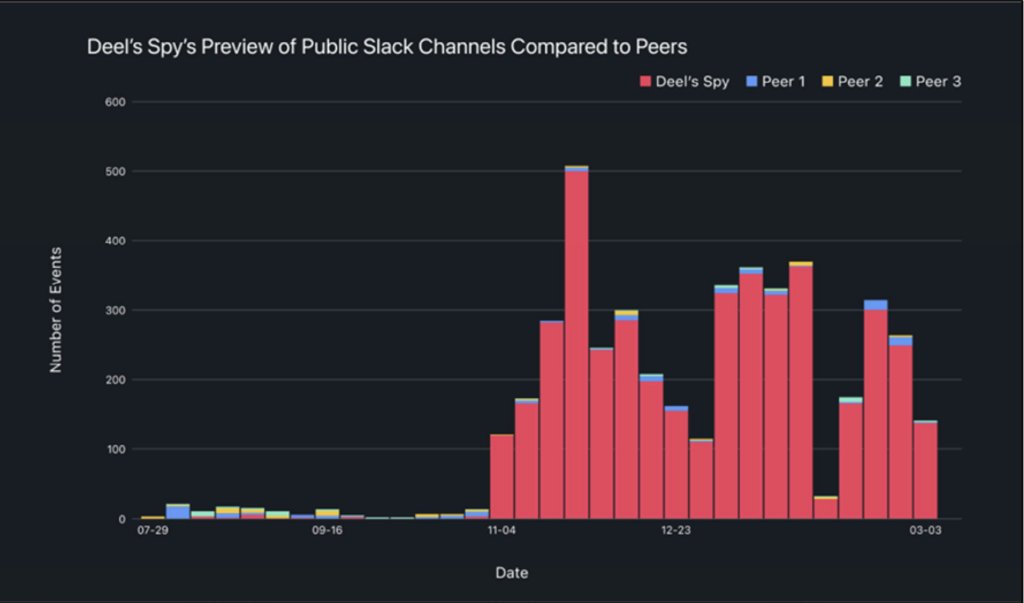
Rippling apparently had suspicions and used an old classic to out the spy. Knowing this individual would immediately react if something injurious was about to happen to Deel, Rippling created a fake Slack channel:
Rippling knew that Deel was most likely to activate its spy if faced with potentially damaging press, and indeed, that is how the spy originally revealed himself. So, to confirm Deel’s involvement, Rippling’s General Counsel sent a legal letter to Deel’s senior leadership identifying a recently established Slack channel called “d-defectors,” in which (the letter implied) Rippling employees were discussing information that Deel would find embarrassing if made public.
In reality, the “d-defectors” channel was not used by Rippling employees and contained no discussions at all. It had never been searched for or accessed by the spy, would not have come up in any of the spy’s previous searches, and the spy had no legitimate reason to access the channel.
Crucially, this legal letter was only sent to three recipients, all associated with Deel: Deel’s Chairman, Chief Financial Officer, and General Counsel (Philippe Bouaziz), Deel’s Head of U.S. Legal (Spiros Komis), and Deel’s outside counsel. Neither the letter nor the #d-defectors channel was known to anyone outside of Rippling’s investigative team and the Deel recipients. Yet, just hours after Rippling sent the letter to Deel’s executives and counsel, Deel’s spy searched for and accessed the #d-defectors channel—proving beyond any doubt that Deel’s top leadership, or someone acting on their behalf, had fed the information on the #ddefectors channel to Deel’s spy inside Rippling.
Flushing the Evidence
What happened next was almost comical. The spy apparently resides in Ireland, and Rippling obtained a court order for the agent to hand over his mobile phone (the suit describes the spy as male).
When served, the spy made some excuse about not having his phone, and then promptly locked himself in the bathroom. While government agents informed him that he’d be going to jail if he didn’t promptly turn over the phone, he deleted evidence from his phone before fleeing the scene.
Rather than comply, D.S. was heard “doing something” on his phone by the independent solicitor, who also heard D.S. flush the toilet— suggesting that D.S. may have attempted to flush his phone down the toilet rather than provide it for inspection. Later that day, Rippling had the plumbing of its Dublin offices inspected, but did not locate any mobile devices
The spy was hired in June 2023, but may have been a “sleeper,” only activated in November 2024.
Why he lay dormant for so long and wasn’t activated until November is not stated in the lawsuit. It’s possible he was hired without any espionage intent. Indeed, Rippling also lays out a pattern of Deel targeting Rippling employees in the same department, so it’s possible Deel began targeting Rippling employees after the spy was originally hired. They may have left the spy in place, while using his info to target other candidates for outright recruitment (the lawsuit says 17 had direct contacts or job offers, often without even an interview), or perhaps as additional spies.
The Russian Connection
How did all of this originally come to light?
On February 18, 2025, an investigative reporter at The Information contacted Rippling about a forthcoming article concerning Deel’s Russia-related sanctions activity, noting he had “been working on a story on Deel for the past few weeks” that “started as an exercise to look into the veracity of that lawsuit I previously reported on.” This reporter was referring to his January 9, 2025, article entitled “Deel Accused of Money Laundering, Sanctions Failures in Lawsuit,” which reported on Damian v. Deel Inc., No. 25-cv-20017 (S.D. Fla. Jan. 3, 2025).
The reporter’s email listed eleven assertions regarding supposed issues at Rippling relating to payments into Russia and other sanctioned jurisdictions. Each individual assertion was followed by internal Rippling Slack messages—thirteen messages in total—that supposedly supported or related to the assertion (the “Shared Slack Messages”). As Rippling explained to the reporter, these assertions did not hold water—to be clear, Rippling has never transmitted a payment to a sanctioned country, individual, entity or bank, including Russia—but the fact that internal Rippling Slack messages (which are only available to Rippling employees) were in the possession of someone other than a Rippling employee caused Rippling to immediately open a security investigation.
Through some elementary forensics, Rippling was able to determine the one IP address that had accessed all of these messages: the spy’s.
The spy further outed himself once The Information broke its article, which involved a company called Tinybird. No one at Rippling had ever done any business with this firm, but the spy – and the spy alone – dutifully searched for it in Rippling’s databases.
The spy is only identified as “D.S.” in the lawsuit, but his identity will quickly come to light. How many Irish males with the title of Global Payroll Compliance Manager at Rippling can there be in the world?
The formal complaint has lots more juicy details and lovingly prepared charts.























Leave a Reply