 In popular tech news, articles with titles such as these have begun to spring up:
In popular tech news, articles with titles such as these have begun to spring up:
- “Twitter has a lot of your data. Here’s what you can do about it.” (CNBC)
- “Delete Your Twitter DMs Now, Warns Security Expert” (Forbes)
- “Twitter: Are You Vulnerable?” (LowEndBox)
- “What happens to your Twitter data now that Elon’s taken over” (Vox)
That’s a situation involving a big tech company that has been taken over by an infantile billionaire whose platform was mainly designed for sharing public information. There are DMs, Twitter authorizations, etc. but in the main, you posted info on Twitter because you wanted it to be public.
However, Facebook is very different. Plenty of people only use the platform to share info with their friends, or in private groups. People have all kinds of non-public stuff on there.
Why am I bringing this up? Was Facebook/Meta hacked?
No but they don’t need to be. As reported in the Wall Street Journal today (non-paywall on CNBC), Meta has fired “dozens” of engineers for unauthorized use of an internal tool that allowed them to take over other user’s accounts.
The tools, the Journal reported, were referred to as “Oops,” a shorthand for Online Operations, and were originally intended for internal and special case use. The system allowed employees to restore any individual user’s access to their rightful account, according to the report.
This apparently turned into cases where “workers accepted thousands of dollars in bribes from hackers to compromise or access user accounts.” You can imagine how unfettered access to any Facebook account, message, photo, or activity log would be a stalker’s dream come true.
For years I’ve read comments online by people who don’t trust cloud providers because the government will use them to spy on them or these cloud companies are building massive behavioral databases. The reality is that it’s the bored junior sysadmin or the perverted graveyard shift content moderator who are going to rifle through your files.
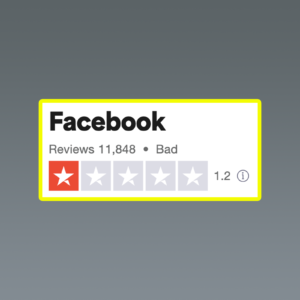
BTW, about that image: Yes, people have reviewed Facebook on TrustPilot and the comments are exactly what you’d expect.





















Leave a Reply