 Every checklist you’ve ever seen for securing your VPS includes “update your system regularly”. But is that one of those “best practices” that is more theoretical than a real-world necessity?
Every checklist you’ve ever seen for securing your VPS includes “update your system regularly”. But is that one of those “best practices” that is more theoretical than a real-world necessity?
To be honest, it’s easy to not get around to running “apt update && apt upgrade”. In my experience, at least with Debian, updates rarely break things but it’s always a small risk. Nevertheless, it requires remembering to do it, spending the commands run, maybe rebooting, etc.
Unfortunately, history has shown time and time again that skipping OS updates can leave even the best admins wide open to disaster. How can we convince you that updating your system regularly is vital? How about with some real-world example from history.
 1. The EternalBlue Exploit (Windows SMBv1 – 2017)
1. The EternalBlue Exploit (Windows SMBv1 – 2017)
In 2017, the infamous WannaCry ransomware spread like wildfire, encrypting data worldwide and demanding Bitcoin payments. It exploited EternalBlue, a vulnerability in the outdated SMBv1 protocol. Incidentally, an exploited for this vulnerability was created by the National Security Agency (NSA), who discovered it but did not disclose it to Microsoft. Unfortunately, a hacker team also discovered it…
But by the time it was widely exploited, Microsoft had already released a patch two months earlier, but many systems remained unpatched.
 2. Dirty COW (Linux Privilege Escalation – 2016)
2. Dirty COW (Linux Privilege Escalation – 2016)
Dirty COW (CVE-2016-5195) was a privilege escalation bug in the Linux kernel. Attackers could exploit it to gain root access, even if they had only limited user privileges. Though it had existed in the Linux kernel for nine years, once discovered, patches were quickly released. Servers left unpatched were vulnerable to full system takeovers.
 3. Heartbleed (OpenSSL – 2014)
3. Heartbleed (OpenSSL – 2014)
Heartbleed was a catastrophic bug in OpenSSL, the library responsible for encrypting much of the web’s HTTPS traffic. The vulnerability allowed attackers to read sensitive data directly from a server’s memory, including private keys and passwords. Patched versions of OpenSSL were released immediately after disclosure. But many admins delayed patching, giving attackers a huge window to exploit servers.
 4. Exim Mail Server Remote Code Execution (CVE-2019-10149)
4. Exim Mail Server Remote Code Execution (CVE-2019-10149)
Exim, a widely used mail transfer agent, had a severe vulnerability allowing unauthenticated remote attackers to execute arbitrary code as root.
A patch was released in June 2019. Unpatched servers were actively targeted within days. Security researchers observed mass scanning campaigns seeking vulnerable Exim instances.
 5. Sudo Vulnerability (Baron Samedit – CVE-2021-3156)
5. Sudo Vulnerability (Baron Samedit – CVE-2021-3156)
A heap-based buffer overflow in sudo, the tool used for executing commands with elevated privileges, allowed unprivileged users to gain root access on many Unix-like systems. The vulnerability existed for nearly a decade but was only disclosed in early 2021. Patched versions were released quickly, but, predictably, many systems remained vulnerable weeks and months later.

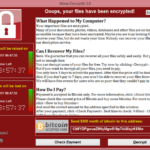 1. The EternalBlue Exploit (Windows SMBv1 – 2017)
1. The EternalBlue Exploit (Windows SMBv1 – 2017) 2. Dirty COW (Linux Privilege Escalation – 2016)
2. Dirty COW (Linux Privilege Escalation – 2016) 3. Heartbleed (OpenSSL – 2014)
3. Heartbleed (OpenSSL – 2014) 4. Exim Mail Server Remote Code Execution (CVE-2019-10149)
4. Exim Mail Server Remote Code Execution (CVE-2019-10149) 5. Sudo Vulnerability (Baron Samedit – CVE-2021-3156)
5. Sudo Vulnerability (Baron Samedit – CVE-2021-3156)



















Leave a Reply