
It’s true – I’m a Porkbun fan. Nicest interface I’ve found and they have either great or at least reasonable pricing. They’re one of the more popular registrars in our community. –raindog308
Hello!
Recently we featured an excellent guest post by Eddie Barksdale at Porkbun. Eddie’s post explains how to install Certbun, which is Porkbun’s alternative to Certbot.
Certbun and Certbot both are Python scripts which install Let’s Encrypt certificates that enable our websites to enjoy secure HTTPS connections. A major difference is that Certbot obtains the certificates from Let’s Encypt at the time the certificates are installed whereas Certbun simply downloads from Porbun certificates previously obtained from Let’s Encrypt by Porkbun. Because Certbun needs to do less than Certbot, Certbun is faster and perhaps less prone to trouble.
It’s obvious that @raindog308 and I are big fans of Porkbun’s wonderful support. Porkbun Support is a great reason to use Certbun. If something is less than completely perfect, an email to the Porkbun Support Team will get everything fixed very quickly.
The steps for installing and using Certbun are well covered in Eddie’s article. When I wanted to try Certbun by following Eddie’s instructions, I started by reading the Certbun script. Then I needed to figure out where in my Apache test server’s filesystem security certificates should be installed. I needed to give Certbun the location for the certificates by adding the certificate location to Certbun’s config.json file.
In the past, I usually have used the Apache web server with Certbot. For my simple use cases, I’ve not yet needed to change the default configurations of either Apache or Certbot. Therefore, I hadn’t learned where Apache wants the certificates to be located because Certbot already seemed to know.
So, for my first Certbun installation I invested some time looking at Apache configuration documentation. Then I got a fun idea. I used Certbot to install its certificates. Next I took a look at the changes Certbot had made to the test server’s /etc and to Apache’s configuration files.
Certbot created /etc/letsencrypt and installed certificates:
root@chi-sm2028tp-htr-4-1:/etc/letsencrypt# ls live/lowend.lol/
cert.pem chain.pem fullchain.pem privkey.pem README
root@chi-sm2028tp-htr-4-1:/etc/letsencrypt# ls -l live/lowend.lol/
total 12
lrwxrwxrwx 1 root root 34 Aug 11 22:24 cert.pem -> ../../archive/lowend.lol/cert2.pem
lrwxrwxrwx 1 root root 35 Aug 11 22:24 chain.pem -> ../../archive/lowend.lol/chain2.pem
lrwxrwxrwx 1 root root 39 Aug 11 22:24 fullchain.pem -> ../../archive/lowend.lol/fullchain2.pem
lrwxrwxrwx 1 root root 37 Aug 11 22:24 privkey.pem -> ../../archive/lowend.lol/privkey2.pem
-rw-r--r-- 1 root root 692 Aug 11 22:18 README
root@chi-sm2028tp-htr-4-1:/etc/letsencrypt#
It’s interesting that the “certificates” which are “live” turn out to be symlinks to “archived” certificates.
Next, I created the /etc/certbun, /etc/certbun/live, and /etc/certbun/live/lowend.lol directories so Certbun could use them.
I set up Certbun’s config.json to use a file structure similar to the structure used by Certbot. Here is my Certbun config.json:
root@chi-sm2028tp-htr-4-1:~/certbun# cat config.json
{ "endpoint":"https://porkbun.com/api/json/v3",
"apikey": "pk1_c3016cef0e5a74339ea332d102fe09230d72ca832ff90512d0889d556b82a116",
"secretapikey": "sk1_9473hbfjokw49ngmcigd0wh39g7hld6lej9kwfkwhyvdwlsufgstshodjsgkslki",
"domain": "lowend.lol",
"domainCertLocation": "/etc/certbun/live/lowend.lol/domain.cert.pem",
"privateKeyLocation": "/etc/certbun/live/lowend.lol/private.key.pem",
"intermediateCertLocation": "/etc/certbun/live/lowend.lol/intermediate.cert.pem",
"publicKeyLocation": "/etc/certbun/live/lowend.lol/public.key.pem",
"commandToReloadWebserver": "systemctl restart apache2"
}
And here are the changes I made in the Apache 2 configuration to switch from the Certbot certificates to the Certbun certificates:
root@chi-sm2028tp-htr-4-1:/etc/apache2/sites-available# cat -n 000-default-le-ssl.conf | tail
30
31
32 ServerName lowend.lol
33 Include /etc/letsencrypt/options-ssl-apache.conf
34 # SSLCertificateFile /etc/letsencrypt/live/lowend.lol/fullchain.pem
35 SSLCertificateFile /etc/certbun/live/lowend.lol/domain.cert.pem
36 # SSLCertificateKeyFile /etc/letsencrypt/live/lowend.lol/privkey.pem
37 SSLCertificateKeyFile /etc/certbun/live/lowend.lol/private.key.pem
38
39
root@chi-sm2028tp-htr-4-1:/etc/apache2/sites-available#
Then, running Certbun downloaded certificates from Porkbun and restarted Apache. Here are the Certbun certificates in /etc/certbun/live (no symlinks yet and no archive yet):
root@chi-sm2028tp-htr-4-1:/etc/certbun# ls -l live/lowend.lol/
total 20
-rw-r--r-- 1 root root 5945 Aug 11 23:25 domain.cert.pem
-rw-r--r-- 1 root root 1826 Aug 11 23:25 intermediate.cert.pem
-rw------- 1 root root 3272 Aug 11 23:25 private.key.pem
-rw-r--r-- 1 root root 800 Aug 11 23:25 public.key.pem
root@chi-sm2028tp-htr-4-1:/etc/certbun#
After I successfully installed and ran both Certbot and Certbun, my tiny but fun hack enabled me to go back and forth between the certificates. All that seemed needed to change certificates was to swap comment hash tags on two lines of a configuration file and restart Apache. See above lines 34, 35, 36, and 37 of /etc/apache2/sites-available/000-default-le-ssl.conf.
As illustrated by the screenshots below, Chrome browser seemed quite happy to accept the unchanged default Certbot / Let’s Encrypt options for both the Certbot and Certbun certificates.
When using the Certbun certificates I could have but did not comment out or change line 33 of 000-default-le-ssl.conf. Thus, the opportunity to study up on /etc/letsencrypt/options-ssl-apache.conf still remains. Indeed, I confess to being curious about some of the default Certbot / Let’s Encrypt settings in /etc/letsencrypt/options-ssl-apache.conf.
The full /etc/letsencrypt/options-ssl-apache.conf file is shown below as the last section of this article. Therefore, this article, together with Eddie’s article, hopefully contains everything needed to use Certbun with Apache in a default configuration without first installing and running Certbot,
Here’s Chrome Browser accepting the certificate issued by Let’s Encrypt via Certbot on August 11:
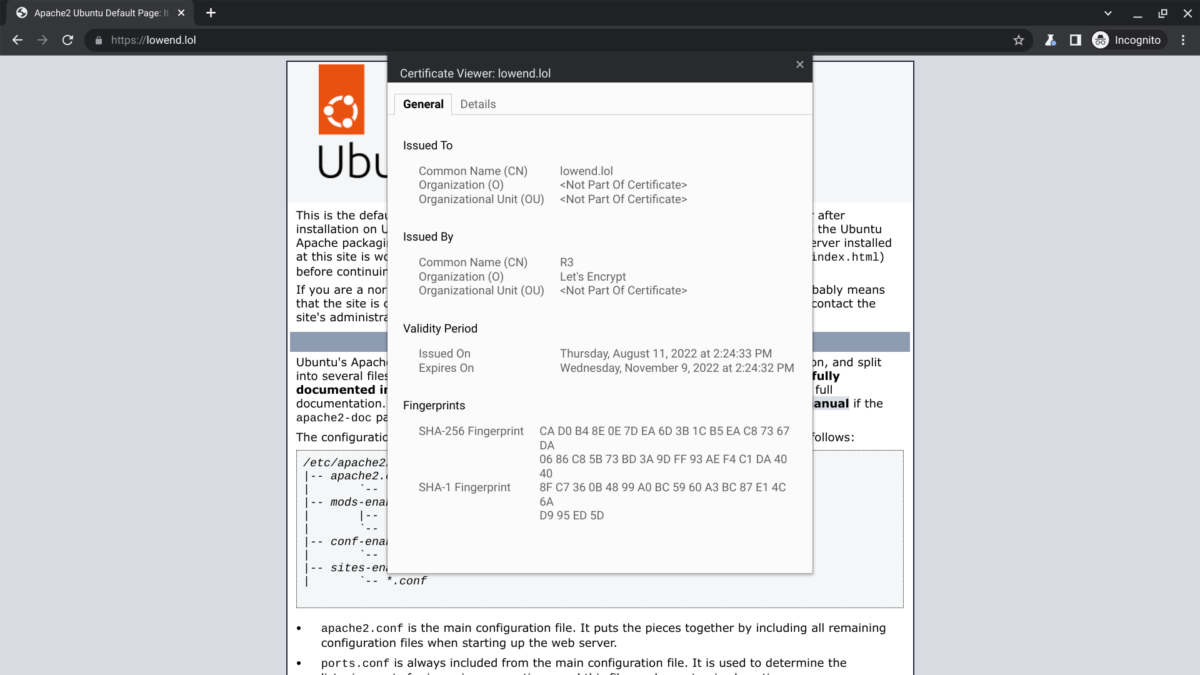
And here’s Chrome browser accepting on August 11 Certbun’s newly downloaded certificate previously obtained from Let’s Encrypt by Porkbun on August 9:
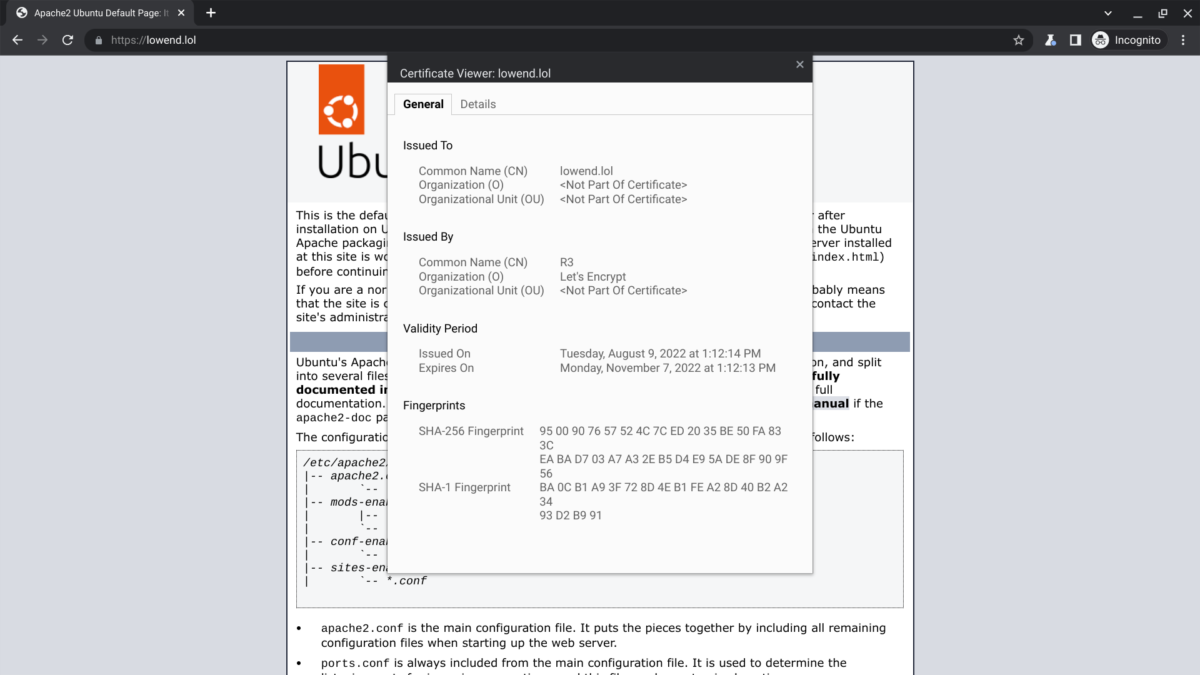
Special Offers
Thanks again to GTHost for the server on which this testing was done. Thanks again to Porkbun and to Eddie Barksdale for Certbun. Thanks again to Phillip and to the entire Support Team at Porkbun for being entirely awesome!
GTHost has provided a promo code for 30% OFF for the 1st month on any GTHost server, valid till 30 Sep 2022. Promo Code: LET22-30
Looking for a new domain name? Visit Porkbun and use the coupon code LOWENDBOX22 for $1 off one new registration, available for new and existing customers!
Certbot Apache Default Configuration in /etc/letsencrypt/
root@chi-sm2028tp-htr-4-1:~# cat -n /etc/letsencrypt/options-ssl-apache.conf
1 # This file contains important security parameters. If you modify this file
2 # manually, Certbot will be unable to automatically provide future security
3 # updates. Instead, Certbot will print and log an error message with a path to
4 # the up-to-date file that you will need to refer to when manually updating
5 # this file.
6
7 SSLEngine on
8
9 # Intermediate configuration, tweak to your needs
10 SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
11 SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
12 SSLHonorCipherOrder off
13 SSLSessionTickets off
14
15 SSLOptions +StrictRequire
16
17 # Add vhost name to log entries:
18 LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-agent}i\"" vhost_combined
19 LogFormat "%v %h %l %u %t \"%r\" %>s %b" vhost_common
root@chi-sm2028tp-htr-4-1:~#























Leave a Reply