A VPN encrypts your traffic, but, at the cost of the VPN provider being in the middle of everything. That provider could still see everything.
Sure, your ISP can now no longer see your traffic, but your VPN provider can.
Of course, nearly every VPN provider says that they won’t look at your traffic, and most advertise a no-logs policy.
The only issue? You have to trust them.
So, if a VPN isn’t the right solution for anonymity, you might be asking yourself:
What’s the Purpose of a VPN?
The real use case of a VPN is the business world. Securing networks, systems, and beyond.
You can control and lock down your WordPress website if you only allow a specific static IP to access it to begin with, for example.
There are also other use cases like improving network routes, changing geolocation, and beyond.
I’m not saying a VPN is worthless. Just not a great choice for anonymity…
It doesn’t matter if it’s:
- NordVPN
- Mullvad
- ProtonVPN
- Surfshark
- TunnelBear
- CyberGhost
- Express VPN
- IVPN
- Or beyond
Sure, your traffic is encrypted through them in the middle…
But all you have is trust.
Tor: The Real Solution to Anonymity
If you’re not already aware of it, Tor stands for The Onion Router. It’s the decentralized internet.
How is it decentralized? Here’s how they explain it:
Tor Browser uses the Tor network to protect your privacy and anonymity. Using the Tor network has two main properties:
- Your internet service provider, and anyone watching your connection locally, will not be able to track your internet activity, including the names and addresses of the websites you visit.
- The operators of the websites and services that you use, and anyone watching them, will see a connection coming from the Tor network instead of your real Internet (IP) address, and will not know who you are unless you explicitly identify yourself.
In addition, Tor Browser is designed to prevent websites from “fingerprinting” or identifying you based on your browser configuration.
By default, Tor Browser does not keep any browsing history. Cookies are only valid for a single session (until Tor Browser is exited or a New Identity is requested).
HOW TOR WORKS
Tor is a network of virtual tunnels that allows you to improve your privacy and security on the Internet. Tor works by sending your traffic through three random servers (also known as relays) in the Tor network. The last relay in the circuit (the “exit relay”) then sends the traffic out onto the public Internet.
The image above illustrates a user browsing to different websites over Tor. The green middle computers represent relays in the Tor network, while the three keys represent the layers of encryption between the user and each relay.
It’s designed so that you blend in and can never be singled out.
Unlike a VPN, there is no one you have to trust. Tor is open source and the network is run by several random people around the world.
It relies on entry, middle, and exit nodes to blend traffic.
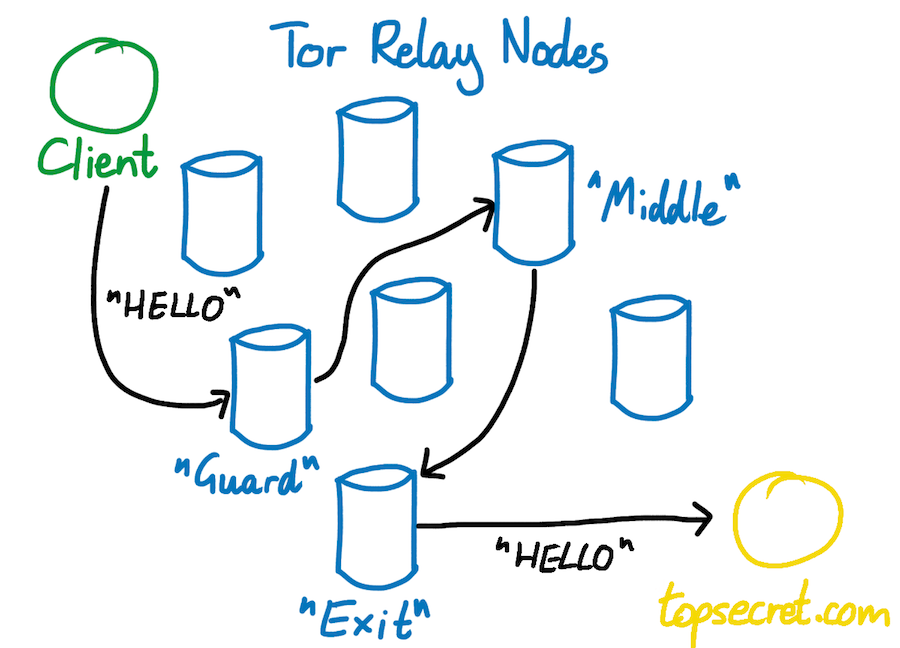
Source: Robert Heaton
(We recently just covered a LowEndTalk member that was convicted of supporting child porn for operating an exit node. It’s worth a read.)
It’s the act of twisting the traffic up together that makes Tor anonymous by design.
What Are the Flaws of Tor?
Tor isn’t a cure-all in terms of anonymity… there are still flaws.
Here’s what they have to say about it:
As mentioned above, it is possible for an observer who can view both you and either the destination website or your Tor exit node to correlate timings of your traffic as it enters the Tor network and also as it exits. Tor does not defend against such a threat model.
In a more limited sense, note that if a censor or law enforcement agency has the ability to obtain specific observation of parts of the network, it is possible for them to verify a suspicion that you talk regularly to your friend by observing traffic at both ends and correlating the timing of only that traffic. Again, this is only useful to verify that parties already suspected of communicating with one another are doing so. In most countries, the suspicion required to obtain a warrant already carries more weight than timing correlation would provide.
Furthermore, since Tor reuses circuits for multiple TCP connections, it is possible to associate non anonymous and anonymous traffic at a given exit node, so be careful about what applications you run concurrently over Tor. Perhaps even run separate Tor clients for these applications.
Ross Ulbricht, the founder of Silk Road, was caught by a combination of bad operation security and what they mention here in regards to the police observing specific connections and times as it connects to the Tor network.
It’s still entirely possible to have the veil pierced when it comes to anonymity using Tor.
Especially when you’re leaving footmarks around everywhere that trace back to you.
Avoiding Footmarks
When it comes to keeping your sacred anonymity, you absolutely have to avoid footprints.
There are a lot of different types of identifying information sites collect, for example:
- IP
- Browser type
- Device type
- Location
There’s more than that, too. That’s just naming a few.
All of that adds up to a footmark of your digital presence that identifies you.
The first step in preventing a footmark is disabling JavaScript. JavaScript should always be disabled on Tor.
If you disable JavaScript, you’re disabling the primary way websites collect data about you.
IPs are only part of the problem.
If you’re one of three people using the Mullvad browser, for example, you’re arguably easier to point out than the average Joe using Google Chrome.
Mullvad, for whatever reason, decided they wanted to partner with Tor and provide nearly practically none of the benefits Tor provides. It seems unlikely that the project ever takes off.
You could gain the same benefits by disabling JavaScript.
Staying Anonymous Online
You’ll need to blend in, and you want no identifying characteristics about your digital presence to be available.
Further, you don’t want to trust anyone at all.
Especially not a private company that’s charging you $10 per month and offering you the world.
By using Tor, you’re using a 100% open-source decentralized project that’s guaranteed to blend your traffic in with others around the world, providing you disable JavaScript, you’ll also have nearly no digital footprint available.
The only thing that’s left is to use basic operation security. Pay attention to obvious links, and use common sense.
A VPN is not providing any more anonymity to you than an SSL certificate is.
P.S. If you’re interested in setting up your own Tor node, we published a guide for that right here.























Leave a Reply