 If you have ever explored the Tor network, you have probably encountered the terms “relay,” “bridge,” and “exit node.” Each plays a critical role in how Tor functions, yet they serve different purposes.
If you have ever explored the Tor network, you have probably encountered the terms “relay,” “bridge,” and “exit node.” Each plays a critical role in how Tor functions, yet they serve different purposes.
If you’re a hardcore Tor user, you probably understand the differences. If you’re just looking to help out the project, you might not. Let’s break the down so you understand which service is right for your VPS.
What is Tor?
Tor (The Onion Router) is a network designed to anonymize internet traffic by routing it through multiple nodes, wrapping each layer of communication in encryption. When you use Tor, your traffic is passed through a sequence of nodes so that no single node knows both who you are and what your traffic contains.
So you might be logged into your PC in Los Angeles, CA but when a forum in Europe sees you, you appear to be coming from Brazil. That’s great for privacy, though not so great for performance. As a user, you’re sacrificing a bit of speed for anonymity.
As a LowEnd VPS operator, you can choose to participate in the project by running a relay, bridge, or exit. The more nodes on the network, the stronger it is. But which?
Tor Relays
Tor relays are the basic building blocks of the Tor network. They pass traffic from one node to another. Bridges and Exits are also relays – they’re just specialized.
There are three types of relays:
Guard (Entry) Relays: These are the first hop in the chain. They know your IP address but not your destination.
Middle Relays: These pass traffic deeper into the network and never know the origin or the final destination.
Exit Relays: These are the final hop. They send traffic from the Tor network to the public internet.
Relays must be publicly listed in the Tor directory. They require bandwidth, uptime, and proper configuration to support the network effectively.
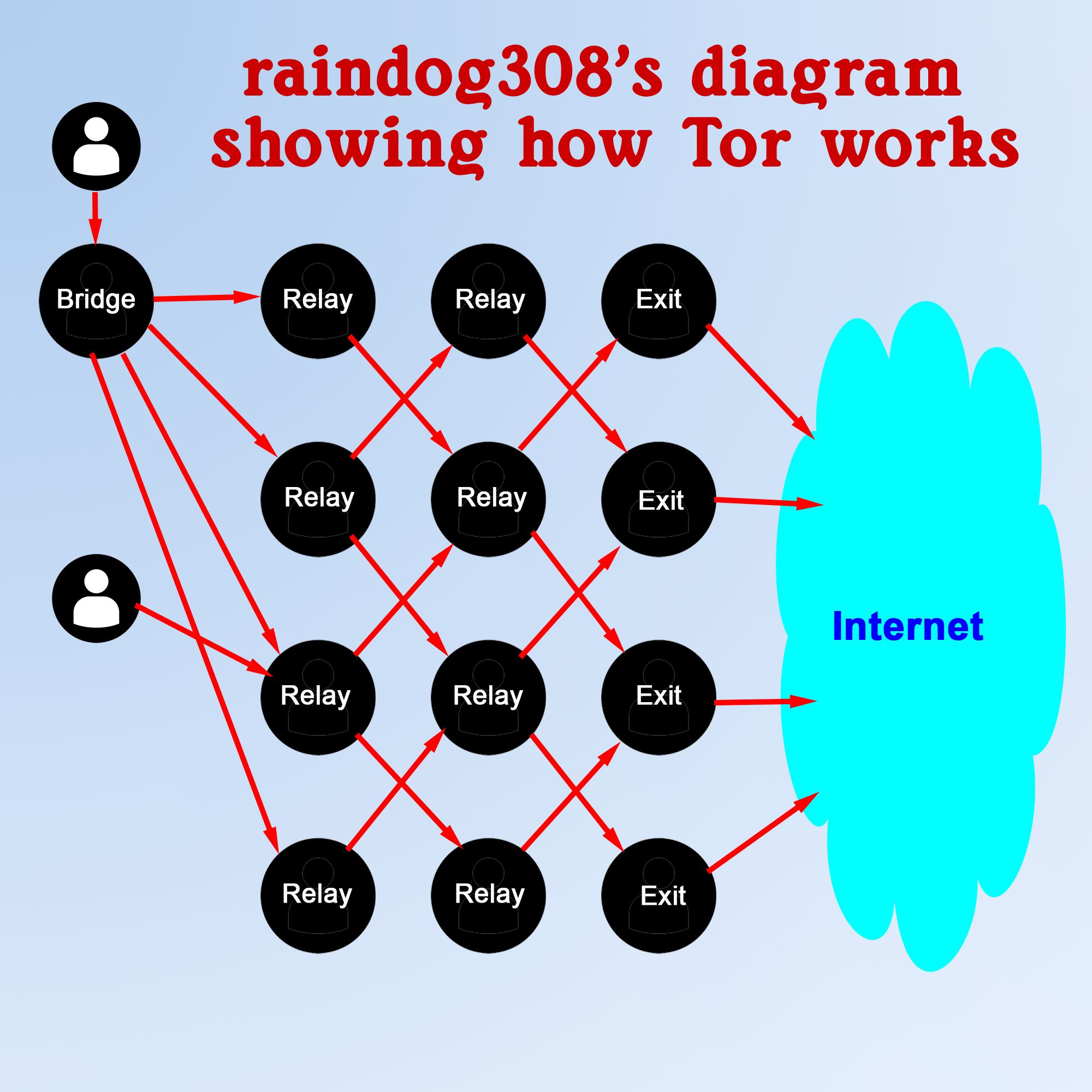
Tor Exit Nodes
Exit nodes are a specific type of relay. They are the last hop before traffic leaves the Tor network and reaches its final destination on the public internet. Exit nodes can see the destination IP and the traffic itself if it is not encrypted (e.g., HTTP traffic).
Because of this visibility, exit node operators can be blamed for traffic that originates from their node. Running an exit node requires careful consideration of legal and abuse-related issues. Many countries hold the exit node operator responsible for any illicit activity that appears to come from their IP address.
Tor Bridges
Bridges are essentially unlisted Tor relays. They are not included in the public directory, making them harder for governments and ISPs to block. Bridges are useful for users in countries or networks that censor access to Tor.
There are two major types of bridges:
Standard Bridges: Hidden from the public directory but otherwise function like regular relays.
Pluggable Transports: These disguise Tor traffic to look like normal web traffic, making it even harder for censors to detect and block connections.
Bridges provide a crucial entry point for users who would otherwise be unable to connect to the Tor network.
Should You Run a Tor Node?
If you want to support the Tor network, running a plain old middle relay is the safest and simplest way. It helps the network without exposing you to the risks associated with exit traffic.
Running a bridge is also a valuable way to help users who are in censored regions gain access to Tor.
If you have the resources and understand the legal implications, you can consider running an exit node. This decision should be made carefully and ideally with the support of an organization familiar with Tor and local laws. You should carefully check your provider’s Terms of Service before running an exit node. Might be worth ticketing in ahead of time to make sure the provider is OK with what you’re doing.





















Leave a Reply