
We told you about GlobalPing last year (6 weeks ago). They describe themselves this way:
Globalping is a platform that allows anyone to run networking commands such as ping, traceroute, dig and mtr on probes distributed all around the world. Our goal is to provide a free and simple API for everyone out there to build interesting networking tools and services.
It’s a distributed set of probes around the world run by volunteers, and you can interact with its API to use these probes to analyze and troubleshoot internetworking issues. The project is run by @jimaek, who you may know from jsdelivr.
Note that you do not need GlobalPing hardware to participate. You can run a probe in a Docker container – see instructions here.
What’s In the Envelope
My GlobalPing probe arrived in a padded envelope from Krakow, Poland. Here’s what was inside:

Included were:
- The GlobalPing unit including an installed MicroSD card.
- A MicroUSB adapter 5V/2A – package says “power supply for RPi Zero”
- A MicroSD card with the OS loaded. In my case, this was a Kingson CANVAS Select Plus 32GB card. I can’t imagine they need anything like 32GB of storage but presumably that’s now the most common card and so getting those is cheaper than 8GB cards.
- A Euro plugged power plug and a US plug adapter
- A short network cable
- Instructions
- Stickers!
Note: My MicroSD card was actually ejected when I opened the package. Just FYI – make sure your card is inserted all the way otherwise there’s no OS for your unit.
The probe is a sealed metal case and there’s a GlobalPing sticker on one side. The case is approximately 5.5cm by 4.5cm and about 3cm high (1-3/4″ by 2-1/8″ and 1-1/4″ tall). I’m using a cloth tape measure I happen to have handy so these are eyeballed approximations.
There’s a USB port which can be used for updates. Read more here. There are no switches or buttons on the case, only power,. network, MicroSD and USB port.


There is absolutely no reason to take it apart, so naturally I did. It’s a small board with a NEO 512M. Apologies for the photo – my phone didn’t like zooming in this far. GlobalPing describes their probes as “An ARM based mini computer in a metal housing”. The Neo 512 is a module I saw on several boards when googling.
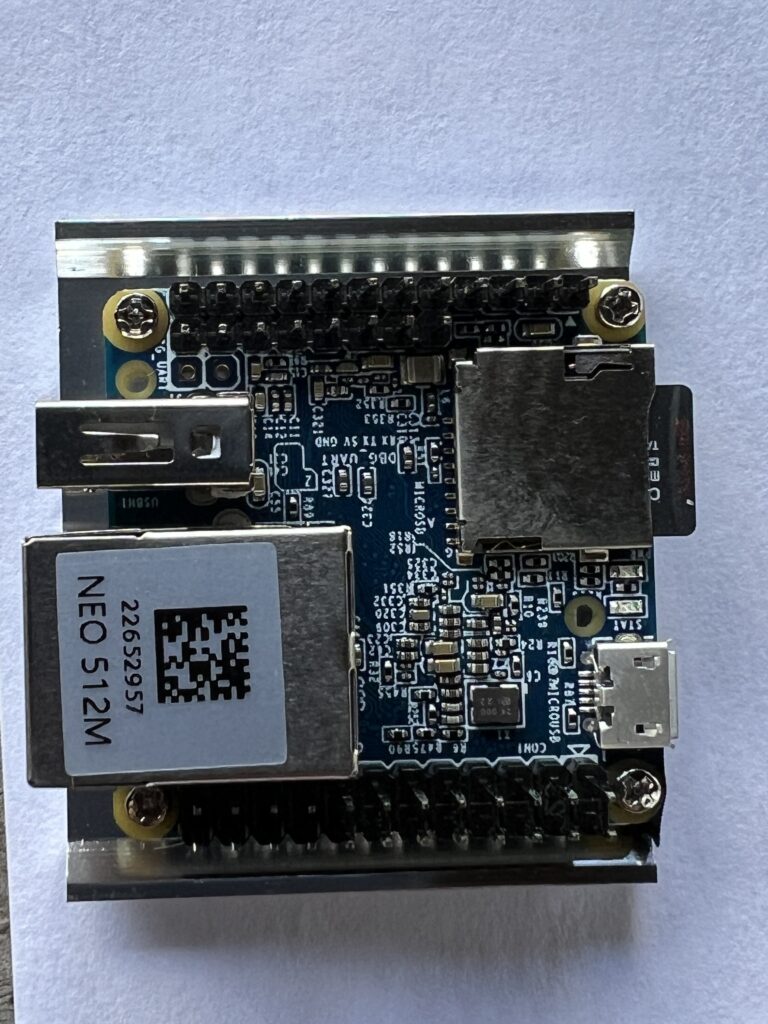

I could probably get more info from the other side, but there’s a heat sink on the bottom and looking at the side view, I can see they’ve got thermal paste. I’m not going to disturb that so that’s as far as I went.
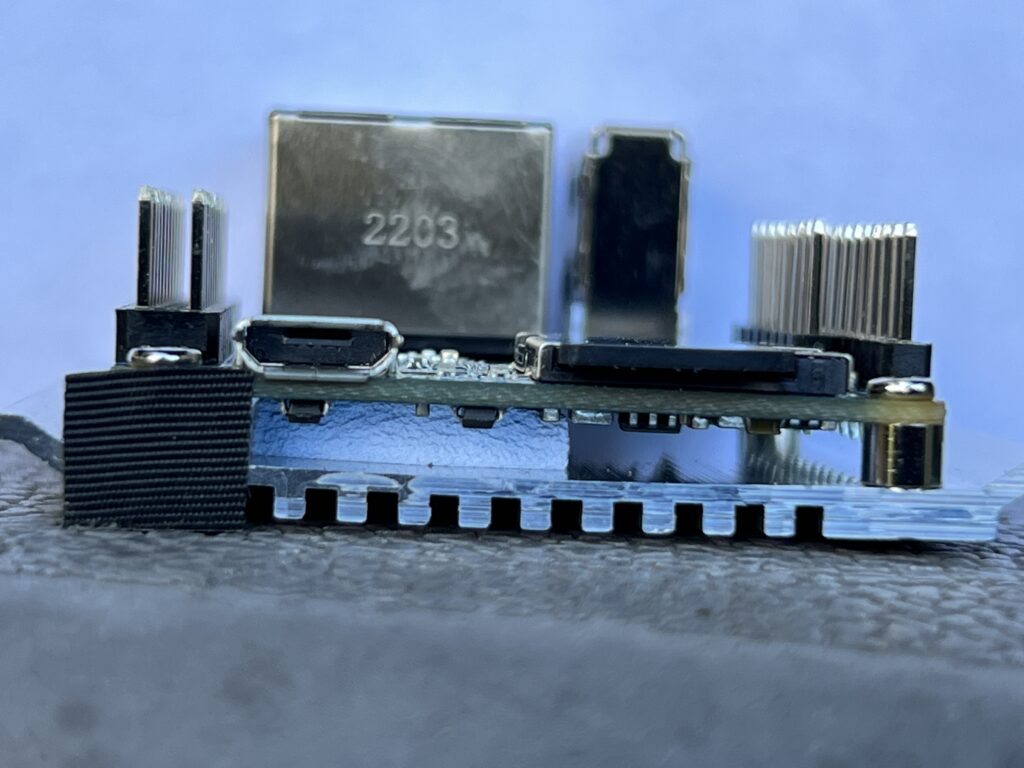
The case is very well designed. You can side the board in and out of it very easily, yet when assembled, there is no rattle.
The power plug is an ugly brick and putting on the US adapter only makes it uglier. Of course, we can’t expect Apple-level custom engineering for a FOSS project! This is going to sit on the power outlet out of sight anyway.

Setup
It’s easy to setup: plug in the power and network cable. The instructions say it takes about 3 minutes to fully boot.

I wanted to know where on the network this thing was, so I booted it, captured the MAC, and then used my DHCP server to assign a static IP. Fortunately, the device identifies itself as “globalping-probe-1234” in its client ID so it’s easy to spot. The 1234 in this case is the last four of the MAC address.
After assigning the IP, I unplugged and replugged the device to pick it up.
After that, I followed the instructions to login to it. You can ssh to logs@IP_ADDRESS without a password. Here’s what you get:
$ ssh logs@192.168.X.X The authenticity of host '192.168.X.X (192.168.X.X)' can't be established. ED25519 key fingerprint is SHA256:0aM7QP6qbVaJV/4i4oGhf2v6GS18vu9YMArjBlRMkcI. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.X.X' (ED25519) to the list of known hosts. Could not chdir to home directory /home/logs: No such file or directory Updating certificates in /etc/ssl/certs... 0 added, 0 removed; done. Running hooks in /etc/ca-certificates/update.d... done. Checking for the latest version Current version 0.10.1 Latest version 0.10.1 [2023-01-01 19:21:44] [INFO] [687] [general] Start probe version 0.10.1 in a production mode [2023-01-01 19:21:45] [DEBUG] [687] [general] connection to API established [2023-01-01 19:21:45] [INFO] [687] [api:connect] connected from (Portland, US, NA) (lat: 45.XXXX long: -122.XXXX)
When I look on GlobalPing’s API page, I see two different probes listed for Portland, Oregon:
[0.10.1] [READY] Portland (OR), US, NA, 7922 -- Comcast Cable Communications, LLC [0.10.1] [READY] Portland (OR), US, NA, 54600 -- Peg Tech
I think I am the first one, as I have Comcast, as there isn’t another Comcast user is on “Peg Tech” (who I had never heard of and has a rather…colorful history). The 7922 and 54600 numbers are the ASNs. It’d be nice if my device had some kind of unique identifier so I could verify it’s working there. If there were many users in Portland, many would probably be on Comcast.
The box is pretty buttoned up. Here’s what a local nmap scan shows:
root@rundeck:~# nmap -p1-65535 192.168.X.X Starting Nmap 7.80 ( https://nmap.org ) at 2023-01-02 09:53 PST Nmap scan report for 192.168.X.X Host is up (0.00089s latency). Not shown: 65534 closed ports PORT STATE SERVICE 22/tcp open ssh MAC Address: 02:3F:30:36:XX:XX (Unknown) Nmap done: 1 IP address (1 host up) scanned in 3.35 seconds
Playing with GlobalPing
You can’t actually do anything on your device other than look at logs, but you can play with the API. When I logged in, it said there were 579 probes available around the world.
The first ten times I requested a ping of google.com with a location of “Portland”, it used my neighbor whose ISP is “Peg Tech” (WordPress munges the JSON, sorry):
PING google.com (142.250.72.206) 56(84) bytes of data.
64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=1 ttl=113 time=1.60 ms
64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=2 ttl=113 time=1.58 ms
64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=3 ttl=113 time=1.58 ms
--- google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 402ms
rtt min/avg/max/mdev = 1.575/1.585/1.602/0.011 ms
{
"id": "5oNHmcDO4VGdxJN7",
"type": "ping",
"status": "finished",
"createdAt": "2023-01-01T19:42:48.316Z",
"updatedAt": "2023-01-01T19:42:49.104Z",
"probesCount": 1,
"results": [
{
"probe": {
"continent": "NA",
"region": "Northern America",
"country": "US",
"state": "OR",
"city": "Portland",
"asn": 54600,
"longitude": -122.6684,
"latitude": 45.5242,
"network": "Peg Tech",
"tags": [],
"resolvers": [
"8.8.8.8",
"8.8.4.4"
]
},
"result": {
"rawOutput": "PING google.com (142.250.72.206) 56(84) bytes of data.\n64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=1 ttl=113 time=1.60 ms\n64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=2 ttl=113 time=1.58 ms\n64 bytes from sfo03s21-in-f14.1e100.net (142.250.72.206): icmp_seq=3 ttl=113 time=1.58 ms\n\n--- google.com ping statistics ---\n3 packets transmitted, 3 received, 0% packet loss, time 402ms\nrtt min/avg/max/mdev = 1.575/1.585/1.602/0.011 ms",
"resolvedAddress": "142.250.72.206",
"resolvedHostname": "sfo03s21-in-f14.1e100.net",
"timings": [
{
"ttl": 113,
"rtt": 1.6
},
{
"ttl": 113,
"rtt": 1.58
},
{
"ttl": 113,
"rtt": 1.58
}
],
"stats": {
"min": 1.575,
"max": 1.602,
"avg": 1.585,
"loss": 0
}
}
}
]
}After setting ASN to 7922, I thought the work was coming from my device. But then I saw it was coming from Illinois, where Comcast also operates. So I added a city filter and things worked as expected. And on my device’s logs:
[2023-01-01 19:38:56] [DEBUG] [687] [general] ping request EYTkITWoJw8Fv6nM received
Note that GlobalPing says “Our project is under active development and not yet ready for production use,” so we’re still early in this story.
Global Probe Network
First, note that not all of the 570 probes are actual hardware probes. You can run GlobalPing in a Docker container. According to @jimaek, only about 150 of the probes listed are GlobalPing hardware.
If you want to run a GlobalPing probe, click here.
Here’s a list of all countries that have 10 or more probes listed as of 1/1/2023, based on the list displayed on the API page:
- US 152
- RU 61
- NL 38
- DE 27
- GB 26
- CA 18
- FR 17
- PL 16
- JP 15
- IN 13
- AU 11
- BR 11
- SG 11
- ES 10
And here’s a full regional breakdown of the 579 online as of 1/1/2023:
- EU 288
- NA 171
- AS 83
- SA 18
- OC 14
- AF 5
I’m not surprised that the US and EU dominate the list. Having Russia at #2 does surprise me. The Oceania numbers are all Australia except for one Kiwi, and the Africa numbers are all Johannesburg with a single Cape Town. Still, it’s cool to see a true global mix and I’m sure these numbers are going to grow and balance out as the project develops.























Feels like a Trojan horse. Designed to get into my home network, do a surveillance, probing, sniffing…
Kinda my initial thought, though I have no doubt it is a well-intentioned project. Can someone give me the tl;dr of what this is useful for?