CloudFlare is a popular CDN/DDoS mitigation service that is widely used in our community. There is a free version that many hobbyists use, and of course you can pay for more services and better protection.
A common perception is that if you put CF in front of your website, you are immune to DDoS attacks. That is true (within the limitations of CF’s capabilities) if you’re on a dedicated server. But for a VPS and especially for shared hosting, the situation is quite different.
Let’s look at some pictures.
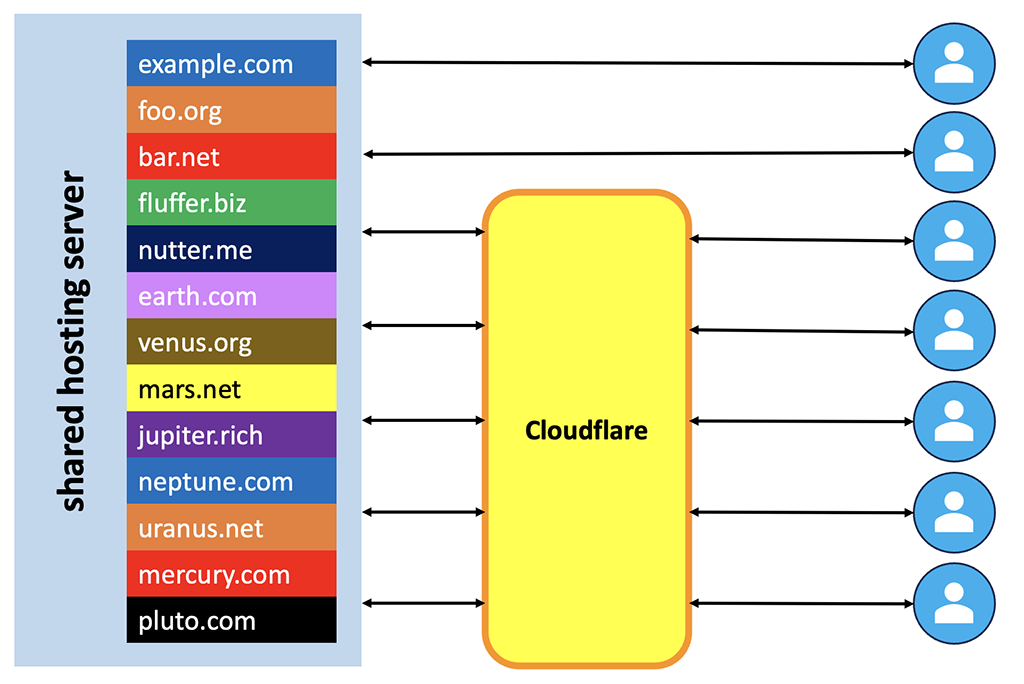
Here’s a typical shared hosting setup. Could be cPanel or it could be DirectAdmin. There’s a server with dozens, perhaps hundreds or even thousands of unrelated domains being served. Some of them are behind CF and some are not. Visitors are either interacting directly with these sites (for example, example.com) or are going to CF.
If the site is 100% static, then CF has no need to talk to the server after its cache is initially populated. But that’s rare these days. Most sites have some interactive or dynamic content.
Now let us interrupt this happy scene by introducing a bad actor.
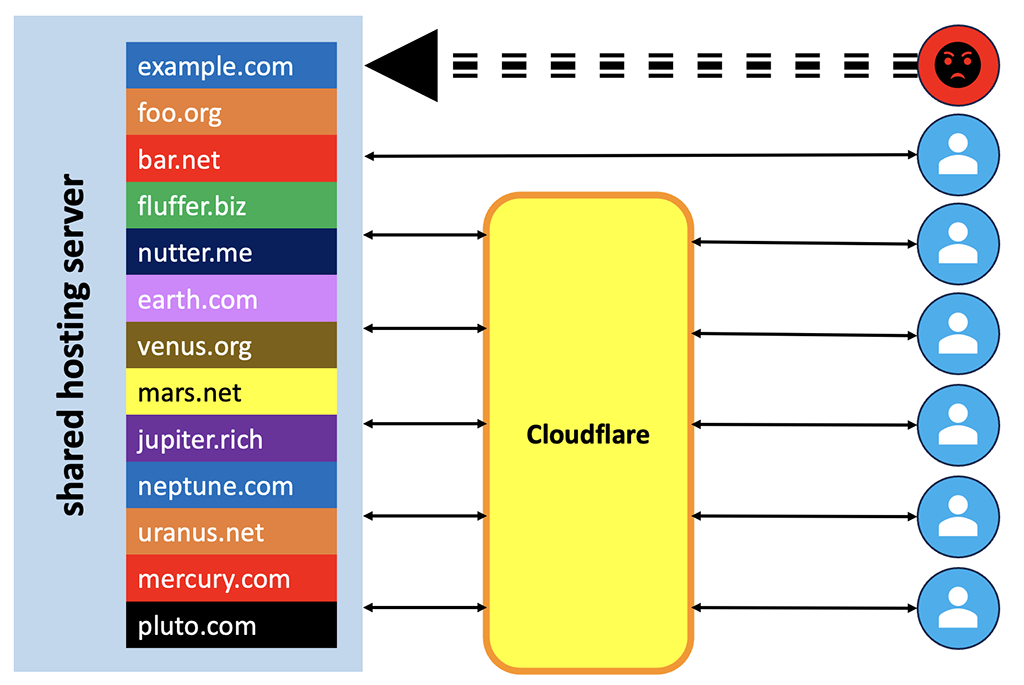
Someone doesn’t like the content on example.com for whatever reason. Could be political, religious, a competitor, or just someone who’s not very mature taking offense at everything. He decides to launch a DDoS attack against that site. It quickly becomes overwhelmed and stops responding.
But here’s the thing…
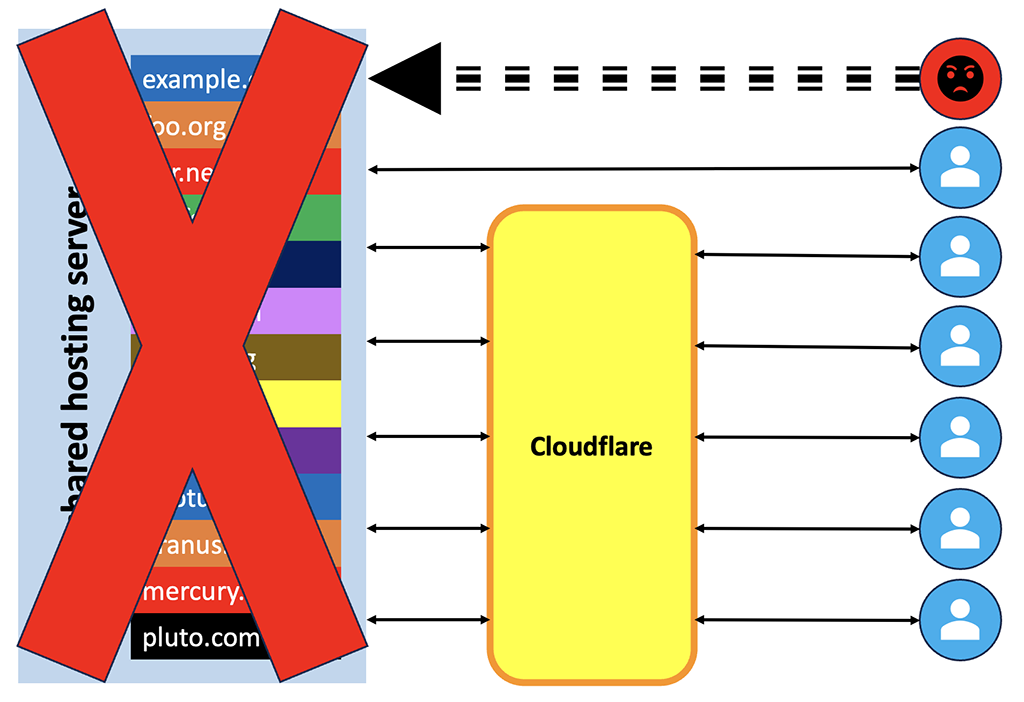
His DDoS attack might swamp the entire shared hosting server, which means that all of the sites on that server stop responding.
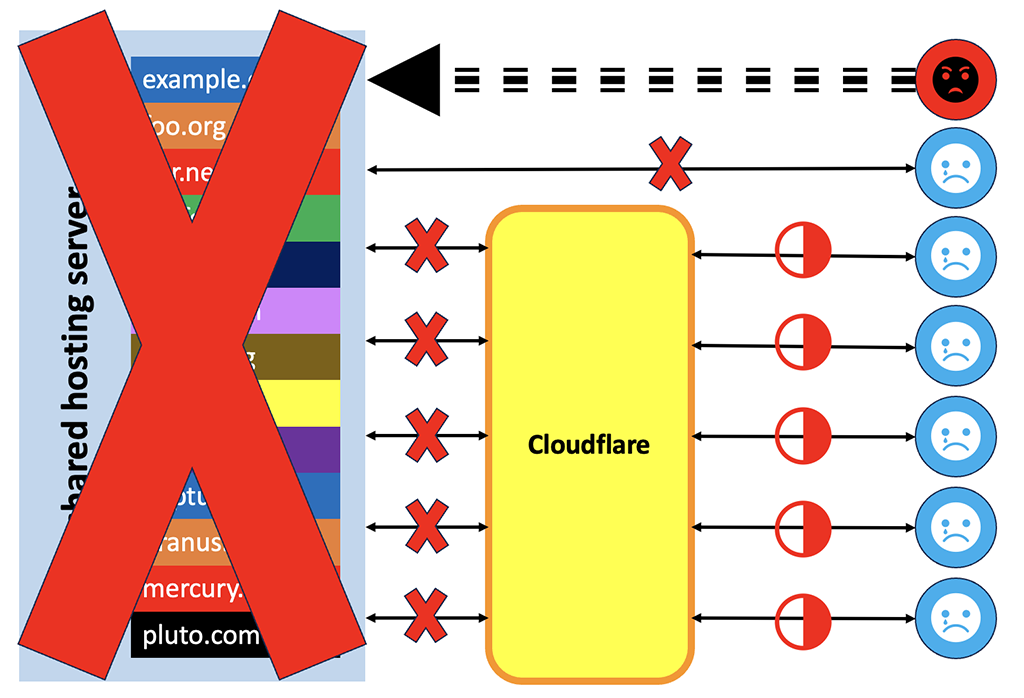
Yes, CF is still up and working great, but once CF can’t talk to the server, none of the dynamic content will come through. Users will get the “you’re viewing a cached copy” message (at best). If your site is WordPress, a forum, etc. then users effectively can’t see it. If you’ve got a shopping cart, you can’t do business.
In short, the problem isn’t that you attracted a DDoS attack. It’s that someone else, who has no DDoS protection such as CloudFlare, did and they’re on the same server as you.
Does this affect VPS servers? Yes, to some extent. It’s possible to swamp a VPS host node. However, there are not as many web sites usually, so the number of domains that might act as magnets for DDoS attacks is smaller. It’s really not unusual to have several thousand sites on a shared hosting server, and you don’t typically see as many on a VPS server. People use VPSes for things other than web servers, though some of these (e.g., game servers) can be DDoS magnets in and of themselves.
The Solution
The best solution is to go with either a dedicated server or a host who providers DDoS protection for their whole network. With a dedicated server, you’re in much more control of your fate. Or sign up for a provider who protects their entire network with DDoS protection.
Related LowEndTalk thread this week: How You Handle Dos & DDoS Attack?





















thanks for the useful article. I bought shared hosting with Racknerd during a holiday special from an ad here a while back and just found this post which led me down a road where found that they posted about ddos protection on shared hosting, https://www.racknerd.com/shared-hosting. glad i read this article as I would have never checked on this since I use cloudflare without being aware of this. thanks.
Hi, an other solution it’s to force everyone to host the website Tru cf 😂😂😂and block from firewall outside connections and allow only cf ☔
AS I DID 😎